Gain Visibility. Reduce Risk. Strengthen Identity Security.
In today’s evolving cyber threat landscape, identity is the new security perimeter. Without full visibility into your attack surface, organisations remain vulnerable to identity-based threats such as credential theft, privilege abuse, and lateral movement attacks.
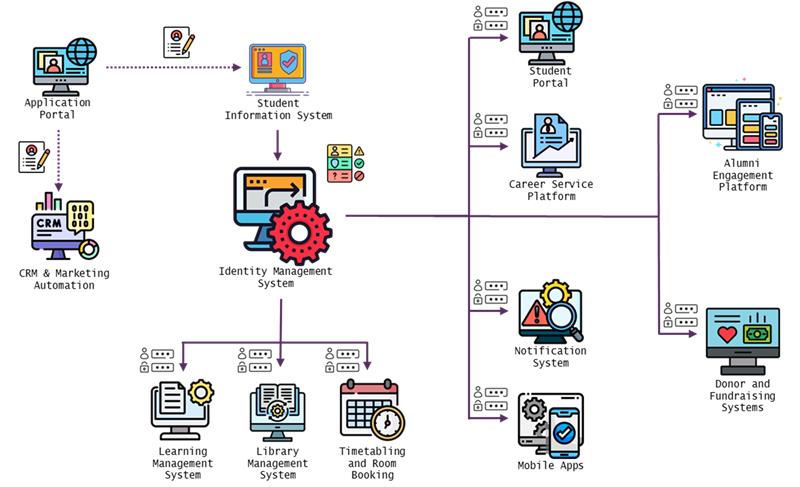
Identity Blueprint
Assertiv’s Identity Security Blueprint provides a structured, actionable plan to secure identities, reduce risk, and improve compliance.
Our staged approach ensures organisations gain full visibility into their identity security risks, address gaps, and implement a strategic roadmap to strengthen their overall security posture.
Attack Surface Visibility & Risk Assessment
Identify all admin, service, and privileged accounts that could be targeted.
Detect MFA gaps, excessive privileges, and misconfigured access controls.
Zero Trust Readiness Review
Assess identity security maturity against Zero Trust principles.
Identify weaknesses in least privilege access, continuous verification, and policy enforcement.
Identity Governance & Access Controls
Define policies for identity lifecycle management.
Establish structured onboarding, offboarding, and access review processes.
Threat Detection & Mitigation Strategies
Identify lateral movement risks, credential abuse, and shadow IT usage.
Recommend real-time monitoring solutions to detect identity-based threats.
Roadmap for Security Maturity & Compliance
Provide a tailored strategy to strengthen IAM security over time.
Align with industry best practices and regulatory requirements.
High-Level, Staged Approach to Assertiv’s Identity Security Blueprint Services
Stage 1: Discovery & Attack Surface Visibility
Objective: Identify all identity-related risks and map the attack surface.
Key Activities:
- Conduct an identity risk assessment to identify admin, service, and privileged accounts.
- Analyse authentication mechanisms, including MFA coverage and legacy protocols.
- Map identity-related attack surfaces, including external and third-party integrations.
- Identify potential lateral movement risks and over-privileged accounts.
Outcome: A comprehensive visibility report outlining identity security risks.
Stage 2: Identity Security Assessment & Gap Analysis
Objective: Compare the current state of identity security against best practices.
Key Activities:
- Benchmark identity security maturity against Zero Trust principles.
- Assess IAM governance policies, access controls, and compliance requirements.
- Identify weaknesses in identity lifecycle management, provisioning, and deprovisioning.
- Detect misconfigurations, weak security hygiene, and policy enforcement gaps.
Outcome: A detailed risk analysis highlighting security gaps and improvement areas.
Stage 3: Threat Detection & Mitigation Strategies
Objective: Implement real-time monitoring and risk reduction measures.
Key Activities:
- Identify and mitigate real-time identity threats, such as credential abuse and lateral movement.
- Implement adaptive access controls to enforce least privilege.
- Strengthen authentication mechanisms, reducing reliance on legacy protocols.
- Define threat response strategies to prevent identity-related breaches.
Outcome: A set of actionable recommendations to reduce identity attack risks.
Stage 4: Roadmap & Implementation Planning
Objective: Develop a long-term strategy for continuous security improvement.
Key Activities:
- Design a phased implementation roadmap tailored to the organisation’s needs.
- Prioritise quick wins while planning for long-term identity security enhancements.
- Align with industry best practices, compliance standards, and regulatory requirements.
- Provide ongoing guidance and best practices to improve identity security resilience.
Outcome: A structured roadmap for maturing identity security over time.
Objective: Identify all identity-related risks and map the attack surface.
Key Activities:
- Conduct an identity risk assessment to identify admin, service, and privileged accounts.
- Analyse authentication mechanisms, including MFA coverage and legacy protocols.
- Map identity-related attack surfaces, including external and third-party integrations.
- Identify potential lateral movement risks and over-privileged accounts.
Outcome: A comprehensive visibility report outlining identity security risks.

Objective: Compare the current state of identity security against best practices.
Key Activities:
- Benchmark identity security maturity against Zero Trust principles.
- Assess IAM governance policies, access controls, and compliance requirements.
- Identify weaknesses in identity lifecycle management, provisioning, and deprovisioning.
- Detect misconfigurations, weak security hygiene, and policy enforcement gaps.
Outcome: A detailed risk analysis highlighting security gaps and improvement areas.
Objective: Implement real-time monitoring and risk reduction measures.
Key Activities:
- Identify and mitigate real-time identity threats, such as credential abuse and lateral movement.
- Implement adaptive access controls to enforce least privilege.
- Strengthen authentication mechanisms, reducing reliance on legacy protocols.
- Define threat response strategies to prevent identity-related breaches.
Outcome: A set of actionable recommendations to reduce identity attack risks.

Objective: Develop a long-term strategy for continuous security improvement.
Key Activities:
- Design a phased implementation roadmap tailored to the organisation’s needs.
- Prioritise quick wins while planning for long-term identity security enhancements.
- Align with industry best practices, compliance standards, and regulatory requirements.
- Provide ongoing guidance and best practices to improve identity security resilience.
Outcome: A structured roadmap for maturing identity security over time.
Where Are You in Your Identity Security Pathway?
Help!
Where do we start?
Start with our
Concept / Discovery Services
We have good IT knowledge, but need support to strategise
and plan.
Enlist our help with our
Strategy / Plan Services
Let’s go!
We know our path forward, but need a team of experts.
Ready to
Design, Build & Deploy
Why Assertiv?
Our staged approach ensures visibility, security, and compliance at every step. We help organisations take control of their identity security posture with a clear, actionable, and strategic framework.
Let’s discuss how we can enhance your identity security—get in touch today!
- Trusted and independent advisor
- Certified for multiple vendor products, and product agnostic
- On-shore, local and onsite team
- Deep product knowledge with over 20 years experience
- Rapid deployment, with high quality results
- Tailored solutions delivered to customer’s requirements
Ready when you are, for a discussion about how we can help.
Australia & New Zealand
Head Office
Level 24
300 Barangaroo Ave
Sydney
+61 1300 181 171
Satellite Offices
Wellington
Melbourne
Singapore
40A Orchard Rd
#03-01 MacDonald House
238838
+65 8670 0592
Copyright © 2024 • Contact Us • Privacy Policy